A few weeks ago I bough access to Pentester Academy labs to boost my skills, since I do not have solid background in countless fields, my job is mainly writing web applications with a little bit of devops tasks (read: I sometimes modify Dockerfiles) and I rarely have an opportunity to observe how “smart people” do it. The very first lab I have taken is 64 bit Linux shellcoding. In first module there is a lab about CPU information in which Vivek uses GDB and warns that in next parts he is going to assume that I am fluent with it and gives a simple task to solve to check one’s skills. Since I have hardly any experience with GDB I thought that working on it with my favourite “trial error and error” method would be fun.
Challenge
The task was simple: compile code below and make it display the “Welcome to SLAE 64-bit course! Please proceed to the next video!” message without entering correct passphrase.
main(int argc, char **argv)
{
char *p ="PentesterAcademyPass";
if (strcmp(argv[1], p) == 0)
{
printf("\nWelcome to the SLAE 64-bit course! Please proceed to the next video!\n");
}
else
{
printf("\nIt's time to review those GDB videos again!\n");
}
return 0;
}
1st take: playing around with assembly
Although I did some assembly on my studies, my knowledge is rather unimpressive: I know that there are some registers that store values, that when function returns it sets some of those, that there are instructions like comparison, basic math, conditional and unconditional jumps (though I do not remember how to make a program take execution path I want). This seemed like a perfect place to start. I set a breakpoint and took a look at what the disassembly gave me.

When the breakpoint at strcmp was hit I tried to make something out of it. OK, call with strcmp@plt followed by two instructions looking like something doing if comparison seemed reasonable. I followed the execution up to this point.

The eax register had something funny in it and I remember that the jne compares something to 0. Having googled how to change a register value I did it and proceeded with the execution.
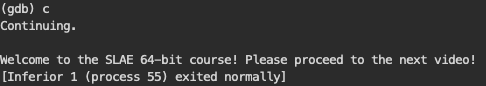
Proud of myself I went back to the video just to hear that I should avoid touching assembly…
2nd, 3rd and next takes
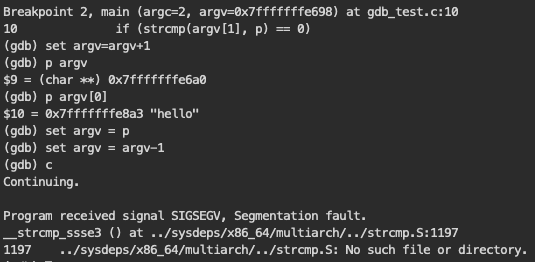
This task seemed to be more and more interesting. How could I achieve the same thing without touching assembly? The first though was again to change the strcmp return value. No luck at this. After stepping into it and giving return 0 command I got a bunch of meaningless errors. On the other hand argv is an array of pointers and p was a pointer, so maybe I could make one point to another?

In GDB “p” is an alias for “print”, so the debugger understood my efforts to set the p pointer value to the address *argv+1 had resulted in another bunch of errors. Forgetting that argv is a pointer to more pointers on the other hand gave me cute segmentation faults like the one above or below.
Finally, when I remembered this fact I managed to set the first pointer in the argv array to the position p pointed.
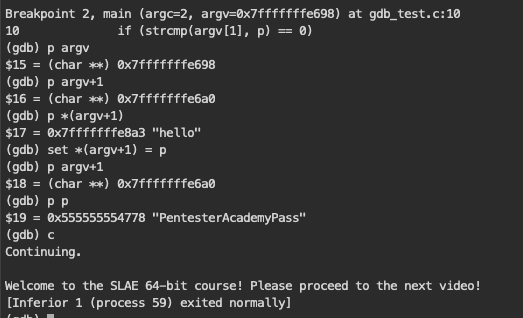
Cool. Second solution in not that long time. The third one was the simplest one. What I did was to tell debugger to go directly to the desired line skipping entire validation. Yes, this was that easy to type jump 11 to get desired effect.

Happy hacking
I definitely will take extra classes on GDB itself, but for now it’s fun to discover everything in my own way. Having worked mostly with graphical debuggers in web app development, I find this low-level stuff fresh. To be honest, I am excited to learn what next labs will bring and post the most interesting solutions on this blog.