
Since the very beginning of the existence of this service I was sure that people visiting me would sooner or later start attacking me. Maybe not with helicopters like in image but in a more intangible way. I’ve also said that I’m OK with it as long as responsible disclosure is used and I’m even to give some reward for discovered vulnerabilities (though I haven’t thought what kind of). I still welcome attempts to join The Hall of Fame 😉
In fact this happened quite quickly and today I want to give you an overview of what techniques are used when attacking my blog and what security measures I take to prevent it.
What attacks do I expect?
The attack vectors I am afraid of are the ones using known security issues or bruteforce login attacks. I do not think anyone would try to burn any unknown exploit on some hardly known blog since it makes more sense to sell it to Zerodium or someone similar.
What are my current security measures?
Most of my security relies on Wordfence plugin which gives following security features:
- Second factor authentication which uses Google authenticator,
- Rate limiting for logging in,
- Blocking bruteforce attacks,
- Blocking attacks based on known vulnerabilities,
- Blocking IPs.
- Warning about outdated plugins and themes.
- Logging attempted attacks.
I’ve chosen Wordfence because I wanted to have 2FA and it had a very short list of known issues.
I don’t hide login panel because this would be inconvenient since I travel and I don’t have a finite list of IPs I am using. Also solutions like changing the url to custom one or using additional authentication to get to the panel do not seem reasonable for me since they give me more of the same protection. If one login could be broken with bruteforce attack, so could two and so could custom urls be found. Therefore I prefer to use rate limiting combined with strong passwords and 2FA.
Apart from that I use a plugin for HTTPS. Although this is more for positioning than against MITM attacks. Also I have a plugin for collecting statistics (no Google tracking, the most I get is approximate geolocation and anonymized IP address – the last octet gets truncated, so I store no personal data).
I have also disabled all services I could on my hosting, like FTP access. And automatically update my WordPress.
I use strong, random passwords generated by KeePassXC and I use a plugin for Firefox/Chrome/Brave/Whatever I’m currently using to fill the password automatically.
There are things I’m not happy with, but they have to wait for a moment.
How am I attacked?
Black sheep hacks mostly gets attacked with simple login attempts, most of which do not even try to log in on existing user.
This happens a few times a week, though recently I observe an increase in the frequency.
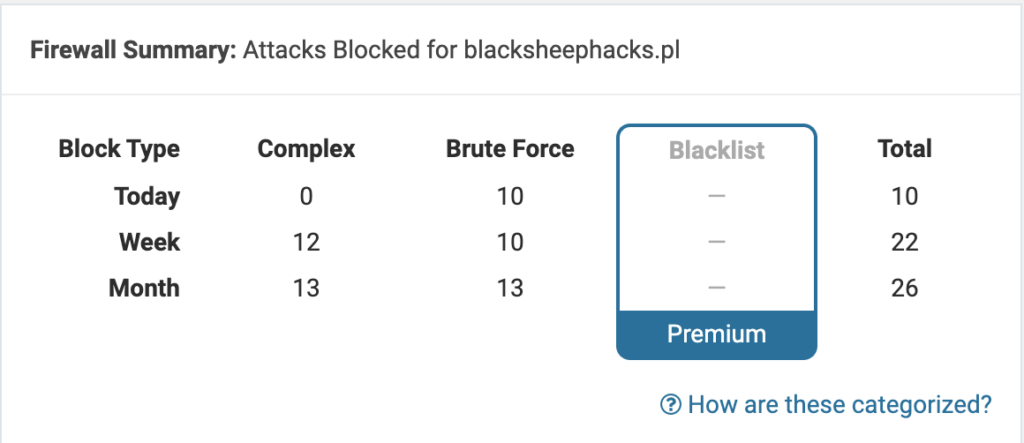
There are also some attacks that try to exploit known vulnerabilities in plugins I don’t use, like social login plugins or Barclaycart:
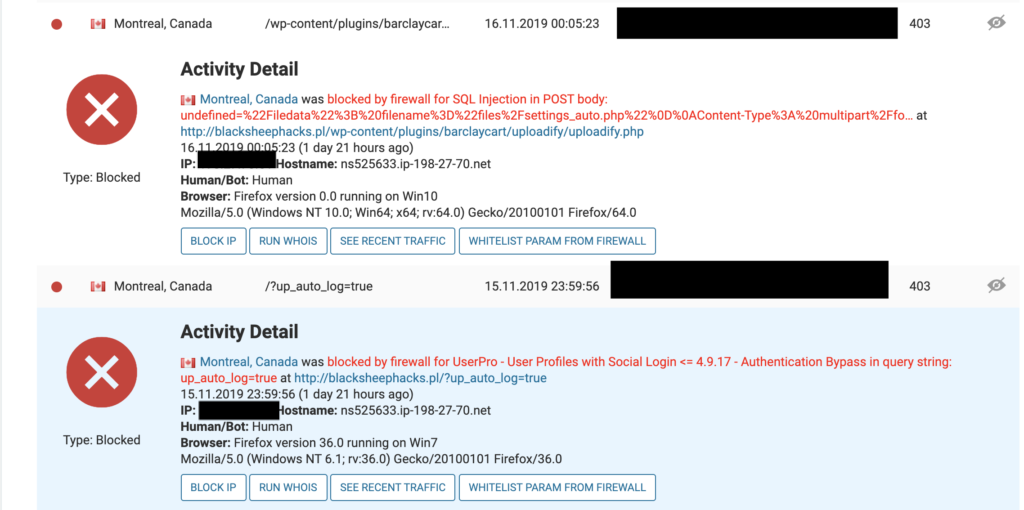
Sometimes these are attacks are classified as conducted by bots like this attempting to exploit LFI in Slider Revolution plugin.

This is an important hint that in the future someone might try to use automated tools like sqlmap against my site and I will have to deal with it.
Summary
That’s the very beginning of my journey through the world of infosec and I see that starting a blog was a good idea. Not only gives me a reason to learn new things, but also it provides me with my first real-world experience on how an attack may look like from a defender’s perspective. Up to now I resorted to fooling around with DVWA and similar projects and here I am the one responsible for foreseeing the possible attacks, taking precautions and monitoring my infrastructure.
These attacks mainly attempt to exploit vulnerabilities which are known ones, so currently I observe no zero-day attacks. Some of the bugs that visitors try to abuse are several years old and most of them attack plugins. Two conclusions drawn at this point are:
- Use password managers. They give you stronger passwords than you could ever come up with. I bet $100 that if I used admin/admin credentials I would have already been hacked.
- Always keep your code up to date (and WordFence really helps me with this one sending notifications whenever a newer version of plugin that I use, is out). Most of the “sophisticated” attacks in fact try to use known issues.
- Use minimal number of plugins that allow you to operate. The fewer the better.
